Home
»Blog Insights
»Understanding HIPAA Compliant for Healthcare App Development: A Comprehensive Guide
Understanding HIPAA Compliant for Healthcare App Development: A Comprehensive Guide
Keyur Patel
September 12, 2025
10 min
The Health Insurance Portability and Accountability Act (HIPAA) is a significant law in the United States concerning the confidentiality of individuals’ health data. HIPAA compliance becomes very essential as more and more fields of healthcare embrace the use of technology. The goal of this blog is to convey the knowledge of HIPAA compliance, its relevance for patients and hospitals, and the procedure for designing HIPAA-compliant mobile applications.
What is the HIPAA Act?
HIPAA, passed in 1996 is an act that aims at restricting the disclosure of patients’ health information without the patient’s permission. It creates the legal framework for the protection of health data on a national level and lays the foundation of how patient information should be treated in the context of the new frontier of technology.
Key Provisions of HIPAA:
- Privacy Rule: This rule sets standards for the protection of individually identifiable health information.
- Security Rule: This rule sets standards for the protection of electronic protected health information (ePHI).
- Breach Notification Rule: This rule requires covered entities to notify affected individuals, the Secretary of Health and Human Services, and sometimes the media of a breach of unsecured PHI.
- Enforcement Rule: This rule includes provisions on compliance and investigation, civil money penalties for HIPAA rules’ violations, and hearings.
What Makes HIPAA Compliance Important?
For Patients
HIPAA compliance is important to protect PHI from unauthorized access, alteration, or destruction. This puts the patients at ease since they are confident that their health information is safe and cannot be disclosed to the wrong people. This trust is basic within the framework of the patient-physician relationship, it makes patients go for treatment and provides crucial information without any form of resistance.
For Hospitals
All hospitals and other medical facilities have to follow the regulations provided by HIPAA to prevent severe legal and financial consequences, especially when it comes to hospital inventory management software. Failure to do so attracts hefty fines, legal consequences, and loss of reputation among other repercussions. EHR software development focuses on creating electronic health record systems that streamline patient data management, enhance clinical workflows, and improve overall healthcare efficiency Further, HIPAA compliance aids in the simplification of the processes within the healthcare organization, better patient record management, and the establishment of privacy and security consciousness.
How to Make HIPAA-Compliant Mobile Apps?
Mobile applications are specifically significant in the delivery of health services in the digital age. HIPAA-compliant mobile application development allows the protection of patients’ information while at the same time embracing the use of applications in the delivery of healthcare services.
Healthcare app development involves creating mobile applications that enhance various aspects of healthcare delivery, including patient management, telemedicine, and wellness tracking. These apps often integrate features such as appointment scheduling, secure messaging, electronic health records (EHR), and health app monitoring tools to provide users with easy access to medical services and information.
Physical Safeguards
Physical controls are critical to protecting the electronic systems, structures that house the systems, and equipment from natural and environmental factors and unauthorized access.
- Facility Access Controls: Adopt measures that restrict physical contact with the electronic information systems and the building or buildings in which the systems are located and at the same time allow authorized access.
- Workstation and Device Security: Implement physical safeguards for all workstations that access ePHI, to restrict access to authorized users.
Technical Safeguards
Technical safeguards involve the technology and related policies and procedures that protect ePHI and control access to it.
- Access Control Measures: Adopt technical measures and strategies on the electronic information systems that contain ePHI in a way that only persons or software programs that are authorized should be permitted to access the information.
- Audit Controls: Implement hardware, software, and/or procedural mechanisms that record and examine activity in information systems that contain or use ePHI.
- Integrity Controls: Implement policies and procedures to protect ePHI from improper alteration or destruction.
Lifecycle of Developing HIPAA-Compliant Healthcare Apps
Creating a HIPAA-compliant mobile application involves a meticulous process to ensure all privacy and security measures are adequately addressed.
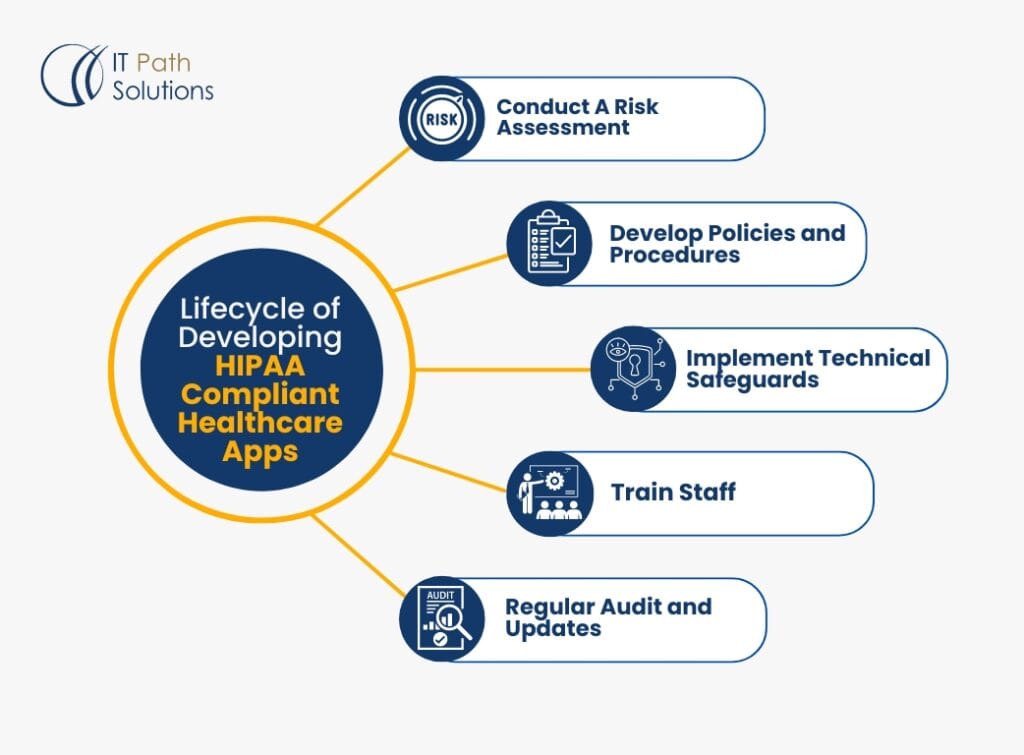
- Conduct a Risk Assessment: Identify and analyze potential risks and vulnerabilities to the confidentiality, integrity, and availability of ePHI.
- Develop Policies and Procedures: Establish and document policies and procedures to address the identified risks and ensure compliance with HIPAA regulations.
- Implement Technical Safeguards: Integrate access controls, encryption, audit controls, and other technical measures to protect ePHI.
- Train Staff: Provide comprehensive training to all employees on HIPAA requirements and the importance of protecting patient information.
- Regular Audits and Updates: Continuously monitor, audit, and update the application and its security measures to address new risks and vulnerabilities.
Ok Now Move on to the next interesting topic feature of HIPAA-compliant
Generic Features of a HIPAA-Compliant Application
To ensure HIPAA compliance, certain features must be integrated into the mobile application.
- Secure User Authentication: Implement robust user authentication mechanisms to ensure that only authorized individuals can access the application.
- Encrypted Data Storage and Transmission: Implement data encryption, to keep the ePHI secure when stored as well as when in transit.
- Regular Audit Trails and Logs: Record activities within the application to ensure the identification and prevention of cases that may depict a breach of application security.
Which Healthcare Apps Should Comply With HIPAA Rules?
HIPAA rules pertain to almost any healthcare-related application. HIPAA rules apply to any app like Doctor On Demand, Telemedicine, or EMR Software Development that processes PHI, regardless of its developer – a healthcare organization, insurance company, or a third party.
Criteria for HIPAA Applicability
- Handling PHI: Apps that store, process, or transmit PHI.
- Covered Entities and Business Associates: Apps developed for or used by healthcare providers, health plans, or healthcare clearinghouses.
- Data Exchange: Apps that facilitate the exchange of PHI between covered entities and/or business associates.
Examples of Healthcare Apps That Must Comply
- Telemedicine and telehealth platforms.
- Electronic Health Record (EHR) systems.
- Health and fitness tracking apps that share data with healthcare providers.
Key Aspects of HIPAA Compliance
Entity
It is very important to understand the entities involved in HIPAA compliance. There are four classes of persons that fall under the act; these are; healthcare providers, health plans, healthcare clearinghouses, and Business associates.
Business associates are third-party entities that are involved in services that involve the use or disclosure of PHI.
Data
HIPAA defines PHI as any information that could be used to identify a particular individual and that is related to that individual’s health status, provision of health care, or payment for the same. This includes all the records concerning the health of the individual, payment information, and any other information that is associated with the health of the patient.
Software Security
To protect software that deals with ePHI, the following measures must be taken: These are user authentication, data encryption, coding standards, and risk assessment to know the threats and ways to address them.
Now, let’s talk about the cost of developing HIPAA compliance.
How Much Does HIPAA Compliance Application Development Cost?
The cost of developing a HIPAA-compliant application can vary widely based on several factors.
Factors Affecting Development Cost
- Complexity of the Application: More complex applications with extensive features will require more time and resources for mobile app developers to develop.
- Security Measures: Implementing robust security measures such as encryption, access controls, and regular audits can increase development costs.
- Compliance and Legal Advice: Ensuring HIPAA compliance often requires consultation with legal and compliance experts.
Average Cost Estimates
The cost of developing a HIPAA-compliant mobile application is an average of $50000 to $150000 based on the requirements and the features of the application.
Key Steps for Making HIPAA-Compliant Applications
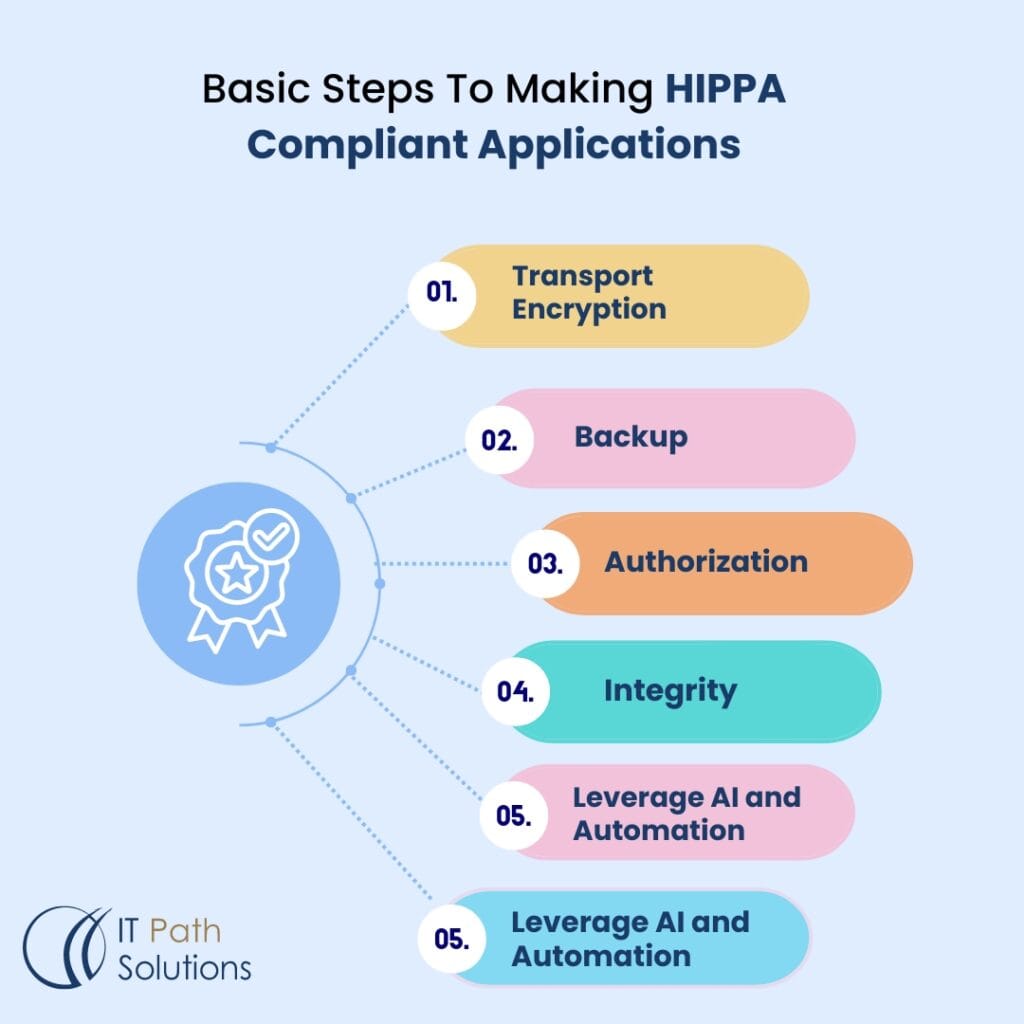
Developers need to follow a detailed process to ensure that applications meet HIPAA compliance standards.
1. Transport Encryption
Make data transfer between systems secure, and use SSL/TLS encryption protocols to secure data in transit.
2. Backup
Backup solutions should be carried out effectively so that if there is loss or a breach then the data can be retrieved. It is suggested that backups should be taken and kept at proper places regularly.
3. Authorization
HIPAA has two major categories that need to be complied with, and they are access control and permissions. In this case, one should use strict authorization measures which would ensure that only those who are authorized can be able to access the information.
4. Integrity
Ensure the confidentiality of ePHI by putting up measures that prevent the altering or destroying of the information. This includes checksum and hash functions to ensure data integrity.
5. Storage Encryption
Encrypt ePHI data stored in the application using the best practices of encryption so that even if the application is compromised, the data cannot be accessed.
6. Disposal
Implement safe disposal methods for obsolete data and devices. This includes secure data deletion and physical destruction of storage media.
Managing PHI Collection, Transmission, and Storage
Handling PHI throughout its lifecycle involves stringent measures to ensure its protection.
Best Practices
- Data Minimization: Collect only the minimum necessary information required for the intended purpose.
- Secure Transmission: Use encryption and secure protocols to transmit PHI.
- Data Storage: Store PHI in encrypted databases with access controls and regular security audits.
- Regular Monitoring: Continuously monitor systems and applications for potential security threats and breaches.
- Compliance Audits: Conduct regular audits to ensure compliance with HIPAA rules and regulations and identify areas for improvement.
Conclusion
HIPAA compliance is a critical aspect of healthcare in the digital age, ensuring the protection of sensitive patient information. By understanding the importance of HIPAA compliance, following best practices, and implementing robust security measures, healthcare providers and developers can create secure, compliant mobile applications that enhance patient care and trust.
FAQs
Q1: What is HIPAA compliance?
HIPAA means compliance with the rules and regulations of the Health Insurance Portability and Accountability Act which aims at the protection of patient health information.
Q2: Who needs to comply with HIPAA?
HIPAA only regulates those that come under the category of the ‘covered entities’ which are the healthcare providers, health plans healthcare clearing houses, and any other third-party Business Associates Agreement that deal with PHI.
Q3: What are the penalties for non-compliance with HIPAA?
The fines for HIPAA non-compliance vary from $100 to $50,000 for each violation with the maximum annual fine of $1. 5 million. Severe violations can also attract criminal charges depending on the gravity of the violation.
Q4: How does encryption help in HIPAA compliance?
Encryption is beneficial in guarding ePHI because it translates data into a form that cannot be understood by anyone who is not authorized to have such information, and it ensures that information is safe both when in transit and when stored.
Q5: What should I do if I suspect a HIPAA violation?
If you have reason to believe that a HIPAA violation has occurred, file a complaint with your organization’s HIPAA compliance officer or the OCR.
Keyur Patel
Co-Founder
Keyur Patel is the director at IT Path Solutions, where he helps businesses develop scalable applications. With his extensive experience and visionary approach, he leads the team to create futuristic solutions. Keyur Patel has exceptional leadership skills and technical expertise in Node.js, .Net, React.js, AI/ML, and PHP frameworks. His dedication to driving digital transformation makes him an invaluable asset to the company.
Get in Touch
Search
Blog Categories
